Reposted from Restore Privacy, on Israel Palestine News, September 15, 2021
Not everyone will find this article interesting, but it is really important because it shows how vulnerable we are to criminal activity on the internet, at least in part because there is no oversight. Maybe for simple cyber theft, but these guys have also been in the espionage business.
A quick anecdote: A decade ago I got a ‘free’ anti spam program on the internet. It was amazing! Initially I realized that the major internet providers can indeed provide a much higher level of spam protection than they admit, probably because it is better for them to let you pay for the extra bandwidth (at least 1/3 over your actual email usage) than expend resources to fix the problem. Ahhh, enlightenment is bitter-sweet. Anyway, this free software worked 100% for a few weeks, then suddenly I was spammed at several times the rate from before I started using the program. Turns out they were an Israeli company engaged in blackmailing the spammers by first blocking them, then after a while accepting payments from them to lift the barrier and provide a list of all their ‘spam relief’ customers.
I have had PIA VPNs (see below) for years. Just the last year or so I have been having trouble with being bounced due to using them. As my host service pointed out (when I was blocked from my own websites one day) this means someone had used ‘my’ address (provided by the VPN service) for the purposes of circulating malware. Or maybe, it was just a mistake. Hmmm – could it be a business model ??? [jb]
Here’s a company run by known cyber-thieves now selling cyber-security devices:
Israeli run Kape Technologies, which formerly distributed malware that infected computers world-wide, has now acquired four different VPN services (which allegedly protect companies’ (and individual’s) online privacy)
A vpn is a form of cybersecurity. It is a false internet address provided by a vpn server, that hides your actual address. Usually you can change your vpn at will so your business does not circulate from a fixed technical location. However, the vpn server and its owner know who and where you are.
Kape is also acquiring ‘review’ websites, which then rank Kape’s VPN holdings at the top of their recommendations… (how smart is that… buy up the product and then the review services)
Israeli billionaire felon Teddy Sagi and Koby Menachemi (connected to Israel’s notorious cyber espionage Unit 8200) are behind the company…
[VPN stands for Virtual Private Network. Companies typically engage a VPN service to better protect their online privacy, while understanding that all of their data — every click, every site, every background app — is being funneled to a single company, whose servers most will never see with their own eyes. More info on VPNs here .]
As is normal in the tech industry, the VPN world is undergoing some major changes and consolidation. The most recent example of this is with ExpressVPN, which announced plans this week to be acquired by Kape Technologies. While this may come as a surprise to many people, it is nothing new in the industry. In fact, Kape has been on a VPN buying spree since 2017.
Unfortunately, many VPN users remain oblivious about the real owners of the VPN they are using as well as the questionable history behind some of these entities. This in-depth report intends to reveal the details for all to see. Here’s what we’ll cover:
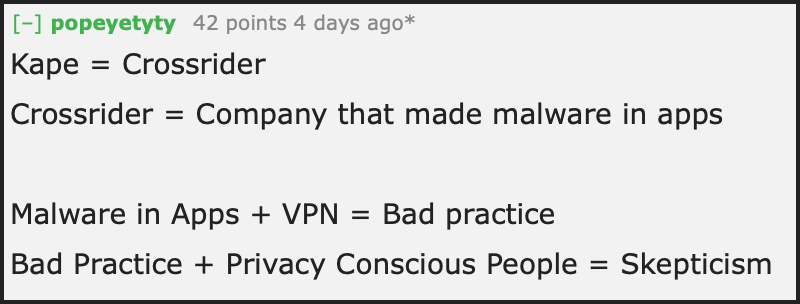
- Kape (formerly Crossrider) was a distributor of malware and adware
- The people behind Kape and Crossrider
- Crossrider begins purchasing VPN services, then changes name to Kape Technologies
- Kape purchases a collection of VPN “review” websites, then changes the rankings
- The future of Kape’s VPN ventures
To get a better understanding of the situation, we must first examine the history of Kape.
Kape (formerly Crossrider) was a distributor of malware and adware
Before 2018, Kape Technologies was called Crossrider and it was an infamous player in the malware industry. You can still find numerous articles about Crossrider’s malware and adware infecting various devices.
Below is an excerpt from a Malwarebytes article that discussed how Crossrider malware infected devices through software bundles:
Crossrider offers a highly configurable method for its clients to monetize their software. The common method to infect end-users is software bundlers. The installers usually resort to browser hijacking. Targeted browsers are Internet Explorer, Firefox, Chrome, and sometimes Opera. Crossrider not only targets Windows machines but Macs as well.
PUP.Optional.Crossrider installs are typically triggered by bundlers that offer software you might be interested in and combine them with adware or other monetizing methods.
In studying Crossrider’s business, it appears that Crossrider profited from infecting devices with malware, which would then use browser hijacking to direct traffic to partner advertisers. This pernicious line of work earned Crossrider a notorious reputation. This business model goes hand-in-hand with data collection, while also abusing the privacy and security of the end-user who suffered the misfortune of being infected with Crossrider malware.
Note: Crossrider malware was still wreaking havoc as late as August 2019. This is about two years after the purchase of CyberGhost VPN and the initial promise to refocus on user privacy. Another post from Malwarebytes explains how Crossrider malware was infecting devices in 2018:
Persistence is the goal of most malware. After all, what good is it to infect a machine if the malware stops running as soon as the computer restarts? There are some cases where that can still be useful (ransomware, for example), but in most cases, that’s not desired behavior. So malware creators are often stuck using the same old methods of persistence that are easy to spot. Sometimes, though, they get creative.
Infection method
This new Crossrider variant doesn’t look like much on the surface. It’s yet another fake Adobe Flash Player installer, looking like the thousands of others we’ve seen over the years.
Opening the installer results in a familiar install process, with nothing unique about it. In the course of installation, it dumps a copy of Advanced Mac Cleaner, which commences to announce that it has found problems with your system using Siri’s voice. (No such problems actually exist, of course.) Safari also pops open and then closes again suspiciously. This is all very blasé, as far as malware goes.
But something interesting has happened behind the scenes. After removing Advanced Mac Cleaner, and removing all the various components of Crossrider that have been littered around the system, there’s still a problem. Safari’s homepage setting is still locked to a Crossrider-related domain, and cannot be changed.
Note: I have not seen any evidence suggesting that Kape is still in the adware/malware business as of today (September 2021).
Now that we’ve examined the business operations of Kape/Crossrider, let’s look at the leadership.
The people behind Kape and Crossrider
The main person behind Kape is Teddy Sagi, an Israeli billionaire who previously spent time in jail for insider trading. Sagi earned much of his wealth from a gambling company called Playtech. Sagi acquired Kape Technologies in 2012 and led it to be a major player in the malware and adware industry.
Interestingly, Sagi is also named in the Panama Papers that detail a “rogue offshore financial industry.”
The other key figure behind Kape is Koby Menachemi. Forbes wrote a good article on Menachemi, detailing his ties to Israeli intelligence and cyber espionage.
Forbes noted the ties that Kape had to Israeli state surveillance entities:
A vast number of companies are affiliated with ad injectors, either packaging their tools or funneling ads down to them. One of the biggest is Crossrider, the majority stake of which is held by billionaire Teddy Sagi, a serial entrepreneur and ex-con who was jailed for insider trading in the 1990s. His biggest money maker to date is gambling software developer Playtech. Co-founder and CEO Koby Menachemi was part of Unit 8200, where he was a developer for three years.
What went unnoticed, until now, is that most of the searchable organisations involved in this potentially dangerous business are based in Israel. They also happen to have links to the nation’s military and its top signals intelligence agency, the Israeli equivalent of the NSA or GCHQ: Unit 8200, which works out of the Israel Defense Forces (IDF).
Interestingly, we also just learned that ExpressVPN’s CIO, Daniel Gericke, also has ties to state surveillance activities. According to Reuters, Gericke and two others, “admitted to violating U.S. hacking laws and prohibitions on selling sensitive military technology” to the United Arab Emirates. According to reports, this “sensitive military technology” helped the UAE spy on dissidents and human rights activists.
“Hackers-for-hire and those who otherwise support such activities in violation of U.S. law should fully expect to be prosecuted for their criminal conduct,” Acting Assistant Attorney General Mark J. Lesko for the Justice Department’s National Security Division said in a statement.
Make of this situation what you will. However, keep in mind that when you use a VPN, you are trusting the service to handle all of your internet traffic and not do anything questionable in the background.
Crossrider begins purchasing VPN services, then changes name to Kape Technologies
Now that you understand the background and leadership behind Kape Technologies, let’s examine its involvement in the VPN industry.
2017: Crossrider purchases CyberGhost VPN for $10 million
Crossrider’s first big VPN acquisition was in March 2017 when it purchased CyberGhost VPN for about $10 million. Originally founded in 2004, CyberGhost was a big player in the industry that experienced rapid growth before it was acquired.
2018: Crossrider changes name to “Kape”
Sometime in 2018, Crossrider decided to change its name to “Kape Technologies” as part of a rebranding effort. Ido Erlichman, the CEO of Kape, admitted that the name change was an attempt to distance Kape from controversial “past activities”:
The decision to rename the company, explains Erlichman was due to the strong association to the past activities of the company as well as the need to enhance the consumer facing brand for the business.
CyberGhost also admitted in a blog post that Crossrider was an “ad tech” company that did the “opposite” of what CyberGhost does (privacy and security):
While CyberGhost focused on privacy and security from day one, Crossrider started out as a company that distributed browser extensions and developed ad tech products. Quite the opposite of what we did.
2018: Kape purchases Zenmate VPN for $5 million
Not being content with just one VPN service, Kape then moved on to purchase Zenmate VPN, based in Germany, for around $5 million.
2019: Kape purchases Private Internet Access for $127 million
The next acquisition came in 2019 when Kape purchased Private Internet Access (PIA) for $127 million in cash and shares. At the time, PIA was a major player in the VPN industry with a substantial user base.
We wrote an article about it back in 2019 and described how many PIA users were upset about the acquisition and did not trust Kape. This screenshot from a PIA user on the PIA subreddit summarizes the situation in a few words.
But the acquisitions were not over…
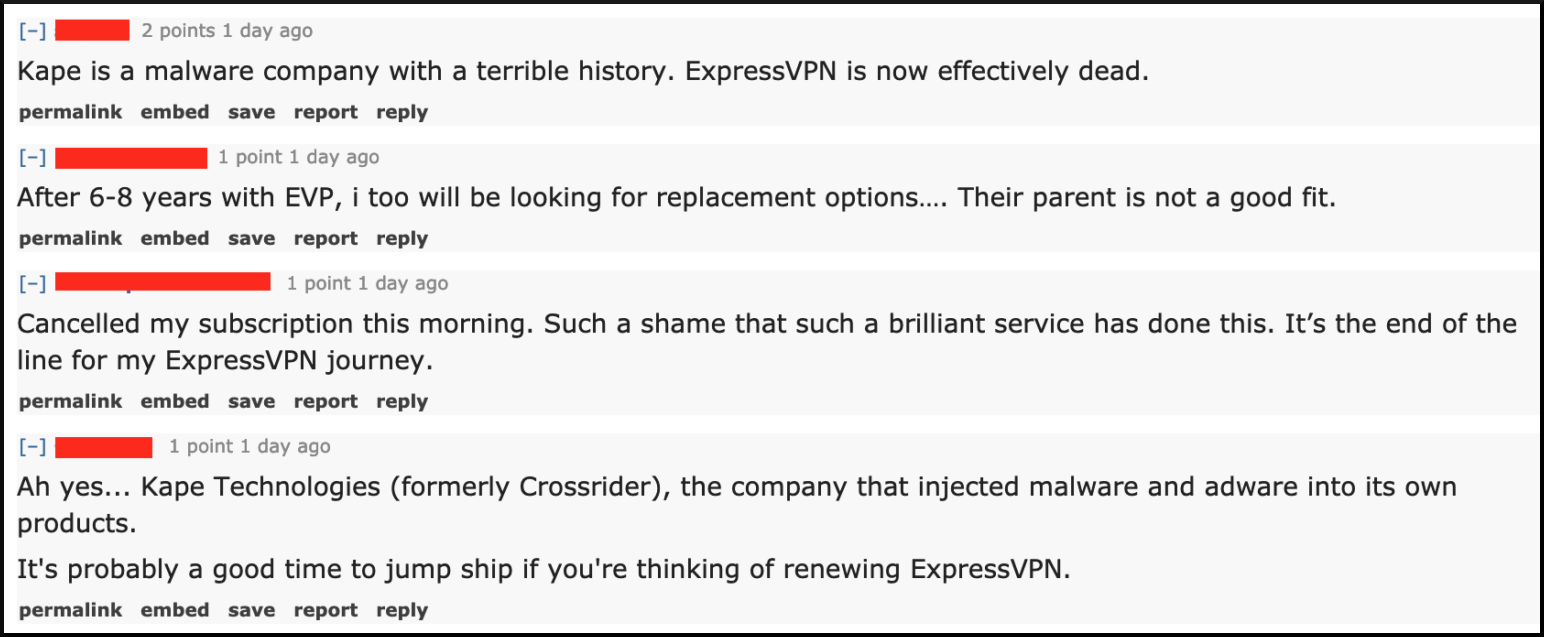
2021: Kape purchases ExpressVPN for $936 million
The latest major VPN acquisition we have for Kape Technologies is ExpressVPN, which it purchased for nearly $1 billion. This is by far the largest VPN acquisition to date and a major addition to Kape’s portfolio.
Watching this same story play out over and over again over the past four years is kind of like Groundhog Day. We generally find two reactions, with the user base being upset and the acquired VPN trying hard to calm everyone down.
1) ExpressVPN users largely seem upset by the news.
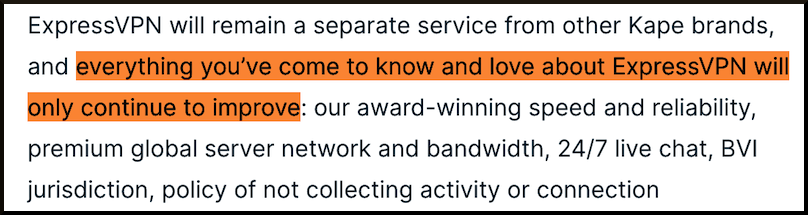
2) ExpressVPN issues canned statements and press releases along the lines of “Don’t be alarmed, everything is good!”
Let’s see how many more times this same story plays out with future VPN acquisitions.
Kape purchases a collection of VPN “review” websites for $149 million, then changes the rankings
In another twist to the plot, Kape Technologies also purchased a collection of VPN review websites in 2021. Yes, you got that right. The parent company that owns these VPNs now also owns a few high-profile websites that “review” and recommend VPNs to users around the world.
This is clearly a conflict of interest, but that goes without saying.
In May 2021, news broke that Kape had purchased a company called Webselenese. Like Kape, Webselenese also operates out of Israel and runs the websites vpnMentor.com and Wizcase.com. Collectively, these two websites have monthly search traffic of around 6.1 million visitors according to Ahrefs traffic analysis tool (September 2021).
Note that there may be other VPN review websites in Kape’s portfolio that we’re not aware of.
Visiting vpnMentor’s homepage today, we find that the parent company’s three large VPN services all hold the top 3 spots in the rankings of the best VPNs for 2021.

Wizcase.com: Similarly, we find the exact same top 3 rankings on Kape’s other website Wizcase.com.
Just a few months ago, both vpnMentor and Wizcase had NordVPN and Surfshark in their top rankings. However, since Kape purchased these websites, we see significant rankings changes that give all of the top 3 spots to Kape’s own VPN companies.
The future of Kape’s VPN ventures
If the past is an indication of the future, Kape will continue to expand its holdings in the cybsersecurity and VPN industry, which only continues to grow. Perhaps in the not-so-distant future, this conglomerate of VPNs and VPN review websites will be spun off and potentially sold as its own company.
In the meantime, there are now millions of VPN subscribers who fall under Kape’s ownership and control. Unfortunately, none of Kape’s VPNs that I have tested have been stand-out performers. The one exception would be ExpressVPN, but it too has fallen behind in the past year and dropped a few spots in our rankings, which will be updated soon to reflect these developments and the latest tests.
Hopefully, this trend in consolidation will slow down as it gives the end-user fewer choices with independently-owned VPN services.